Latest Uber Hack Reinforces Importance of User Training
Uber was hacked (again) last week, resulting in an embarrassing data breach that spread quickly through social media and the news. There is far too much about this latest hack to analyze in a quick post here, but this incident is an important case study in the importance of user education. The user domain will always be the biggest threat to cybersecurity, since people are often inherently trusting and can be easily tricked by skilled attackers.
Reports indicate that the hacker who carried out last Thursday’s attack on Uber was an 18-year old who used the user domain as the entry vector. The attacker reportedly used a multi-factor authentication (MFA) fatigue attack, then contacted the employee to implore him to approve the MFA push alert. Uber is allegedly using Duo for MFA, which has the option of pushing a notification to an app on the user’s phone which can be approved or declined.
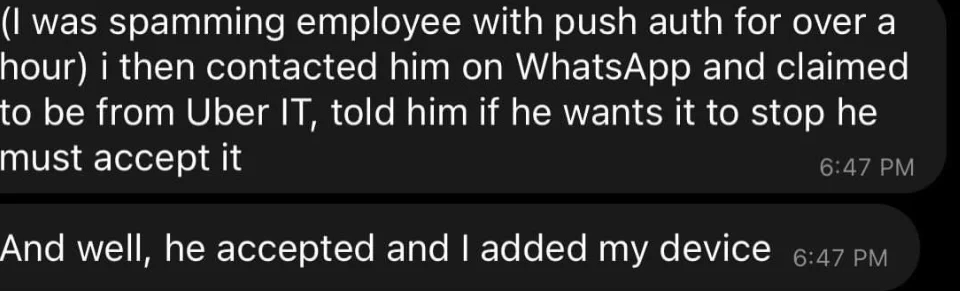
This incident shows that MFA, in itself, is not a fool-proof way of stopping unauthorized intrusion. While the MFA did its job in this case, and stopped the attacker in his tracks, in the end it proved to be useless since the user approved the MFA notification. The issue comes down to user training. Without knowing how Uber implements its MFA, it’s safe to assume that MFA is forced on employees with little to no training about what MFA is and how it works.
I’ve discussed before how MFA is a powerful tool, but it only works well when the user understands how it works. With the growing popularity of MFA, my assumption is that many companies are forcing MFA upon their employees and users without educating them about how the feature works. Users should be taught, in a non-technical way, what MFA is, how it works, and more importantly, what actions will prompt an MFA notification, in the case of Duo.
Users should be taught that if they receive an MFA notification and they are not actively trying to log into their account, there is something suspicious happening and they should contact IT immediately. An account administrator will never ask a user to approve an MFA notification or provide them with a time-based one-time password (TOTP). Users should never give out their TOTP to anyone, even if that person claims to be from IT. There should not exist any system that requires an administrator to ask a user for his/her TOTP.
The second point is how the attacker gained access to the account to begin with. It isn’t clear how this happened, but my guess is that it happened thanks to password reuse. If a password to a work account was reused across personal accounts and then one of those personal accounts was compromised and the credentials published on the dark web, anyone could easily reuse the password and access the work account. To get around password expirations, it’s common practice for users to simply increment a number appended to the end of their password every time the password expires. If the entirety of the password is not checked for reuse and, for example Password!1 is considered uniquely different to Password!2, then this type of password incrementation is allowed by the credential management system.
The way to avoid password reuse is through a password manager. Each account a user has should have a unique password that is stored in the password manager. The password vault should be protected by strong encryption (on the service end), MFA and a long passphrase. Overall length is a better characteristic of a strong password rather than mere complexity. A large number of special characters in a password does not necessarily increase the difficulty of brute force cracking the password but is more likely to result in a user writing the password down since it is difficult to remember. For example, the password of P@5$w0rd, while 8 characters in length and full of special characters and numbers, would take approximately 8 hours to brute force. In comparison, the passphrase of thisisareally$ecurePassword would take approximately 15 nonillion (I had to look it up, too) years to brute force. Try it for yourself at Security.org. The added benefit is that passphrases are easier to remember and therefore less tempting to write down somewhere.